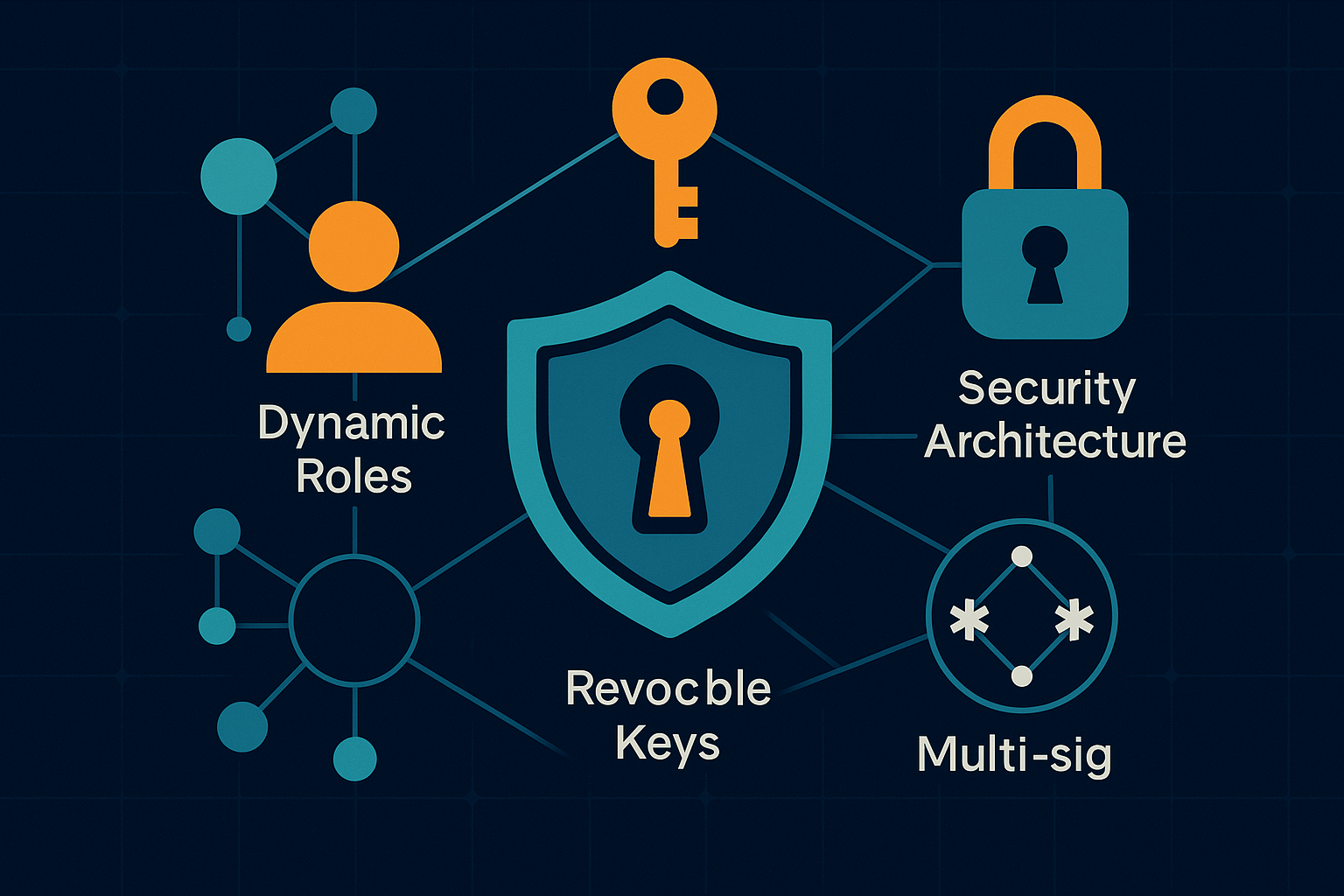
Great tech is useless if it can’t keep your assets safe. That’s why WorthyTrust’s first design principle is uncompromising security. Instead of bolting on protections after launch, we embed them directly into the smart-contract architecture. The result is a layered defense model—dynamic roles, revocable keys, and multi-signature controls—that shields every programmable trust from human error, insider abuse, and external attack. In this deep dive, we’ll unpack each layer, show how they work together, and explain why our approach sets a new standard for on-chain estate planning.
The Threat Model: Know Your Adversaries
Trust contracts sit at the intersection of valuable assets and public blockchains. That makes them a magnet for:
- External hackers hunting for vulnerable code paths
- Internal actors (grantors, trustees, or beneficiaries) who might misbehave
- Key-loss events—the silent killer of many crypto estates
- Protocol-level shocks such as chain forks or oracle failures
Our security stack addresses every one of these vectors without slowing down day-to-day management.
Dynamic Roles: Flexible Authority, Minimal Risk
Traditional trusts assign fixed powers: grantor funds the vehicle, trustee manages it, beneficiaries wait for distributions. That rigidity becomes a liability when life changes. WorthyTrust’s dynamic-role system treats each permission—deposit, withdraw, amend, pause—as a modular capability you can grant, time-limit, or revoke in seconds.
- Grantor keys can pause the contract or rotate trustees but never touch beneficiary payouts once conditions lock.
- Trustee keys may execute routine tasks (e.g., rebalancing, gas-funding) yet have zero access to principal.
- Beneficiary keys are view-only until triggers fire—preventing premature withdrawals.
Because roles live as variables, not hard-coded addresses, you can update them on-chain without redeploying or redepositing assets.
Revocable Keys: Fire and Hire at Will
Losing a hardware wallet or parting ways with a trustee shouldn’t endanger decades-long estate plans. Each active key inside WorthyTrust carries a built-in revocation circuit:
- Initiation: An authorized role (often the grantor or a quorum of guardians) submits a revoke transaction.
- Grace period: The contract holds the request for a user-set interval—anywhere from one hour to seven days—allowing time to cancel in case of hijacking.
- Finalization: Once the countdown ends, the key loses all privileges and a replacement address (if supplied) slides into place.
Every step is logged on-chain for full auditability, so there’s never ambiguity about who controls what.
Multi-Signature Governance: No Single Point of Failure
While dynamic roles and revocations handle everyday operations, multi-sig governance underpins the core vault logic. Key features include:
- N-of-M thresholds: Set a 2-of-3 scheme for small families, a 5-of-7 for DAOs, or any mix that fits your governance culture.
- Role-weighted signatures: Grantor votes might count double, or a beneficiary bloc can override a rogue trustee—your rules, your math.
- On-chain execution: Once the signature threshold is met, the vault acts immediately; there’s no waiting for off-chain coordination.
This structure eliminates the “not your keys, not your coins” problem while still guarding against lost keys or unilateral mistakes.
Key-Management Best Practices
WorthyTrust can’t save a seed phrase left in a drawer, but we do make best-practice hygiene the path of least resistance:
- Hardware-wallet enforcement: The UI flags hot-wallet attempts for high-privilege roles and recommends cold storage.
- Social-recovery guardians: Optional smart contracts allow friends, lawyers, or corporate officers to restore access if you lose every key.
- Shamir secret-sharing: Enterprise users can split the master seed into shards held by separate executives—no single holder, no single compromise.
Formal Verification & Continuous Audits
Every contract version passes through three gates before production:
- Static-analysis scanning for known anti-patterns.
- Formal-verification proofs that critical invariants—like “funds never leave without required signatures”—always hold.
- Independent audits by tier-one security firms, with published reports and GitHub issues tracked in the open.
We also run a public bug-bounty program. If an ethical hacker finds a vulnerability first, they get paid and users stay safe.
Defense-in-Depth, Not Death-by-Complexity
Security features lose value if they confuse users. Each WorthyTrust control lives behind a clean dashboard toggle or slider: pick quorum numbers, set revocation periods, add or remove keys, all without touching code. You get institutional-grade defense in consumer-grade packaging.
Conclusion
Most crypto projects tack on security; WorthyTrust bakes it in. Dynamic roles let power shift with life’s realities, revocable keys erase irreversible mistakes, and multi-sig governance ensures no one can act alone—while formal verification and continuous audits keep the math honest. The upshot is a programmable trust that’s as hard to hack as it is easy to run.
Protect your legacy with infrastructure you can actually trust.
Spin up a vault on WorthyTrust.io and lock in security that scales from family estates to DAO treasuries—no compromises, no single points of failure.